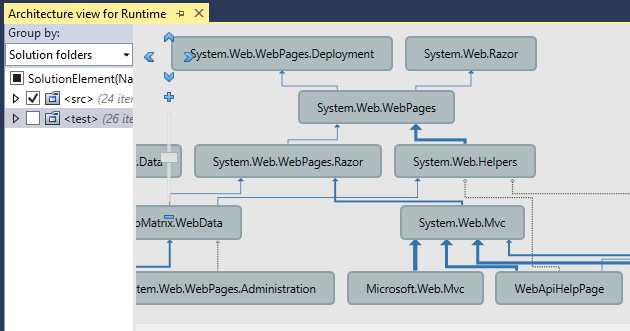
Do you work with legacy code? You might ask, what legacy code is. It is a good question with many different answers:
- Code which is using outdated languages, technologies, libraries, APIs, e.g. COBOL programs;
- Old code
- Code which was written by another team or developer
- Code which has no documented requirements
- Code not covered with automated tests
- Messy code
- Any code (“code becomes legacy as soon as it is written”)
So the definition is a little bit vague. Usually legacy code has few of these properties: old code, written by developers who no longer work for the company, without documented requirements, without tests, built on top of an old technology platform.
Continue reading →